INCIDENT MANAGEMENT
Taxonomy
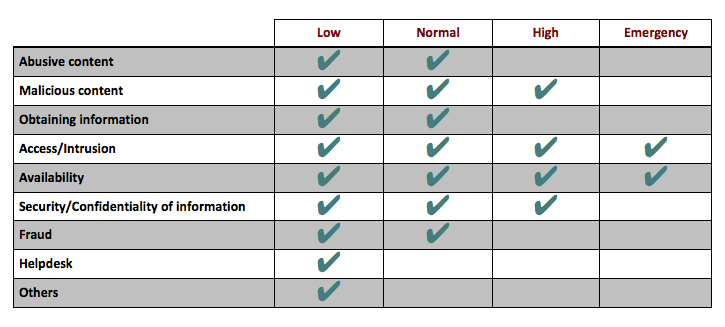
Depending on the type of report received, it will be rated as one of the following
- Abusive content: incidents that show evident signs of spam, contain offensive comments or incite sexual child abuse, violence and/or sexual offences.
- Malicious content: problems associated with viruses, trojans, worms, spyware, bots and code injection.
- Obtaining information: scans are the most common. Those related to the use of sniffers, social engineering and brute force attacks are also included in this rating.
- Access/Intrusion: incidents revealing clear access to privileged accounts, non-privileged accounts, the compromising of applications or 0-day attack.
- Availability: denial of service attacks such as DoS and DDoS.
- Security/Confidentiality of information: problems related to information access and/or unauthorised modification.
- Fraud: reports that are connected to unauthorised use, copyright, identity theft, phishing or credential thefts.
- Helpdesk: incidents containing technical queries or which are merely informative. Also civil or criminal complaints.
- Other: reports in which the RedIRIS CERT is recorded as a witness, but should not take action because it does not fall under its sphere of activity. Also included in this classification those complaint which have not evidence or these are not contrasted.
Priorities
- Emergency: incidents the resolution of which cannot be postponed. Incidents of this type are processed in parallel if there are several, and all available resources are used for their resolution.
Examples: those that endanger human life, national security or Internet infrastructure. To date, all incidents that required immediate action due to their speed and scope of distribution were also considered emergencies.
- High priority: those that due to their features require attention before others, even if subsequently detected. They are kept in a separate high-priority incidents queue, and those with lower priority will not be processed until these are addressed. High-priority incidents are processed in series.
Examples: those incidents in which there is infiltration of a privileged account or a denial of service.
- Normal priority: by default, incidents are handled in series by order of arrival, if one of higher priority does not require attention. A normal priority incident can get high-priority rating if unattended for a long time.
Examples: all incidents not classified as high-priority or emergency where the attacker has gained access to an external computer system. Also included are persistent network scans.
- Low priority: low-priority incidents are handled in series by order of arrival, if one of higher priority does not require attention. A low-priority incident will be automatically closed if unattended for a long time.
Examples: isolated incident attempts, where the attacker has not achieved its purpose and is not likely to do so.
List of priorities and taxonomies
The prioritisation of an incident may vary over time depending on any new information available about it.
Therefore, this relationship is intended to be merely indicative and may be altered in cases where the RedIRIS security team deems appropriate, taking into account the extent and severity of the incident.
 |